Kamran Sharief
What is a Social Networking Site? Definition, Uses, Features and More
Social Networking Site Definition A Social Networking Site is a social structure composed of people, organizations, and entities that are…
How to Become a Network Engineer? Qualifications, Experience and More
The job of a network engineer involves designing and overseeing computer networks, with a focus on high-level planning and…
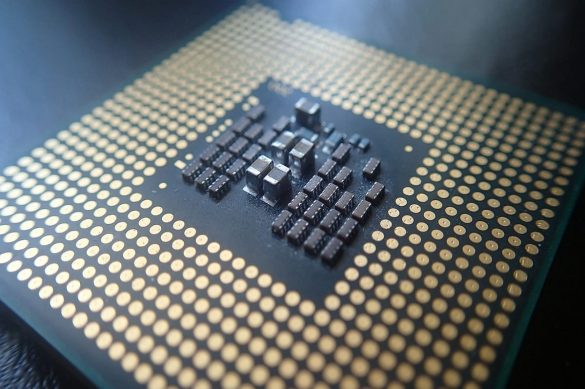
What is a Central Processing Unit (CPU)? Definition, Function and More
CPU Definition CPU stands for Central Processing Unit. With that denomination, the hardware is known whose function is to interpret…
Best Tig Welder Under 2000 – Review by Computer Tech Reviews
Welcome to 2019, where the world has come so far that almost every budget product has become advanced and is…
6 Best Smartwatches you can Wear on the Beach – [2024]
Best Smartwatches You Can Wear On The Beach Smartwatch is a computerized watch that gives numerous different highlights other than…
What is an Operating System? Definition, Types and More
Operating System Definition An Operating System is known as OS. And also, controls the operation of a computer. It is…
7 Effective Ways to Increase Social Engagement
At this point, the majority of businesses understand the importance of marketing on social media. They know that at least…
What is Smart Home Automation?-Definition, Benefits, Features and More
Smart Home Automation Definition Smart home automation uses smart devices and wireless communication to automate tasks. It lets you control…
What is Bespoke Software?- Definition, Uses, Features and More
Bespoke Software Definition Bespoke software is an essential factor in each company. You, as the owner of your own company,…
Top 5 E-Commerce Business Ideas to Make Money in 2019
E-Commerce Business Ideas Do you want to turn your fortune by building an E-Commerce business that sells products all over…
What is Accessibility? – Definition, Uses, Features and More
Accessibility Definition Accessibility is the quality of what is accessible. The adjective accessible, meanwhile, refers to what is simple understanding…
What is Cyberspace? – Definition, Features and More
cyberspace Definition The term cyberspace refers to an environment where the entities and objects that exist within the global computer…
Recent Posts
Proceso Administrativo – Brief Explanation
What is the Proceso Administrativo? Proceso Administrativo is a Spanish word. In English, it is known as an Administrative process….
8 Easy Ways Your Business Can Save Money
Every business wants to save money – it’s a universal goal. From small start-ups to multinational corporations, managers are working…




![image result for 6 Best Smartwatches you can Wear on the Beach-[2019]](https://www.computertechreviews.com/wp-content/uploads/2019/10/image-result-for-best-smart-watches-you-can-wear-on-beach-585x393.jpg)








