Data Privacy Write for Us

Data privacy has emerged as a crucial concern in today’s digital environment. People and companies are producing large volumes of personal data due to the growing usage of social media, cloud storage, the Internet, and online transactions. But this also calls into question the methods used to gather, store, distribute, and safeguard this data.
“Data Privacy” refers to people’s right to manage their data and choose how businesses, governments, and outside parties utilize it. Preventing cyberattacks, upholding legal requirements, and preserving confidence depends on protecting data privacy.
Why Is Data Privacy Important?
-
Safeguarding Individual Data
If it ends up in the wrong hands, personal information, including names, addresses, bank account information, and medical records, might be exploited.
-
Preventing Fraud and Identity Theft
Cybercriminals frequently utilize stolen personal information for illicit purposes, like phishing scams and unapproved bank transactions.
-
Observance of Data Regulations
Governments worldwide have implemented data privacy regulations such as the CCPA in California, the GDPR in Europe, and HIPAA in the US healthcare industry to protect consumer information. Legal repercussions and harm to one’s reputation may result from noncompliance.
-
Increasing Customer Trust
Companies that put data privacy first win over customers, strengthening brand loyalty and giving them a competitive advantage.
-
Defense Against Monitoring and Surveillance
Governments and businesses gather large volumes of user data for monitoring and advertising. Users can safeguard their digital traces with the aid of data privacy.
Common Data Privacy Challenges
- Data Breaches & Cyberattacks
- Inadequate Security Measures
- Data Misuse by Companies
- Lack of Awareness Among Users
- Government Surveillance & Data Collection
Best Practices for Ensuring Data Privacy
Individuals:
- Use Strong Passwords: Enable two-factor authentication (2FA) for additional security.
- Be Cautious About Sharing Information: Limit the amount of personal data shared on social media and online platforms.
- Use Encrypted Messaging Apps: Opt for privacy-focused apps like Signal, Telegram, or WhatsApp with end-to-end encryption.
- Enable Privacy Settings: Adjust privacy settings on social media to restrict data collection.
- Avoid Public Wi-Fi for Sensitive Transactions: Use a VPN (Virtual Private Network) for secure browsing.
Businesses & Organizations:
- Implement Strong Data Encryption: Secure stored and transmitted data with AES-256 encryption.
- Comply with Data Privacy Laws: Follow GDPR, CCPA, HIPAA, and other regulations to avoid legal penalties.
- Limit Data Collection: Only collect essential user data and avoid storing unnecessary information.
- Train Employees on Data Security: Conduct regular phishing prevention and cybersecurity workshops.
- Regularly Update Security Protocols: Install the latest firewalls, anti-malware software, and security patches.
Future of Data Privacy
Data privacy policies are constantly changing due to blockchain, cybersecurity, and artificial intelligence (AI) developments. Governments and corporations are spending money on decentralized data storage, privacy-focused browsers (like Brave), and more stringent data legislation to improve privacy protection.
But as technology develops, new dangers appear. Maintaining current knowledge of data privacy best practices and proactively safeguarding sensitive data are essential for both individuals and enterprises.
How to Submit Your Articles?
To Write for Us, you can email us at contact@computertechreviews.com
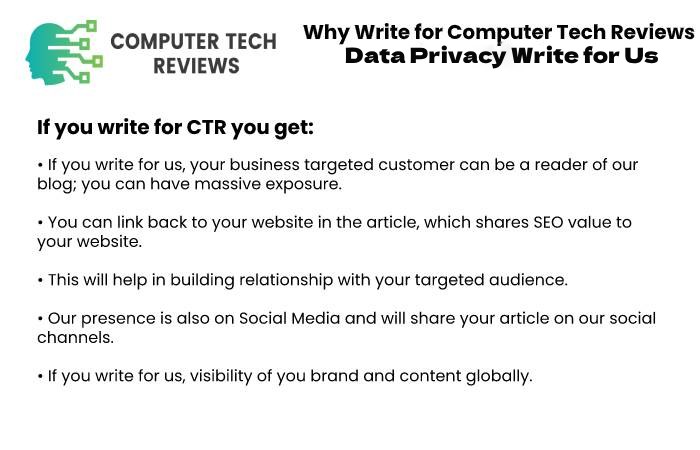
Why Write for Computer Tech Reviews – Data Privacy Write for Us
Search Terms Related to Data Privacy Write for Us
- Personally Identifiable Information (PII
- General Data Protection Regulation (GDPR
- California Consumer Privacy Act (CCPA
- Data Breach
- Encryption
- Data Anonymization
- Privacy Policy
- Cookies
- Data Minimization
- Third-Party Data Sharing
- Consent Management
- Data Subject Access Request (DSAR
- Privacy by Design
- Data Controller
- Data Processor.
- Data Portability
- Data Protection Officer (DPO
- Cross-Border Data Transfer
- Data Retention Policy
Search Terms for Data Privacy Write for Us
- write for us
- guest post
- guest article
- guest post opportunities
- contributing writer
- want to write for
- submit blog post
- contribute to our site
- guest column
- submit content
- submit your content
- guest posts wanted
- guest poster wanted
- accepting guest posts
- writers wanted
- articles wanted
- become an author
- become guest writer
- become a contributor
- submit guest post
- submit an article
- submit article
- guest author
- send a tip
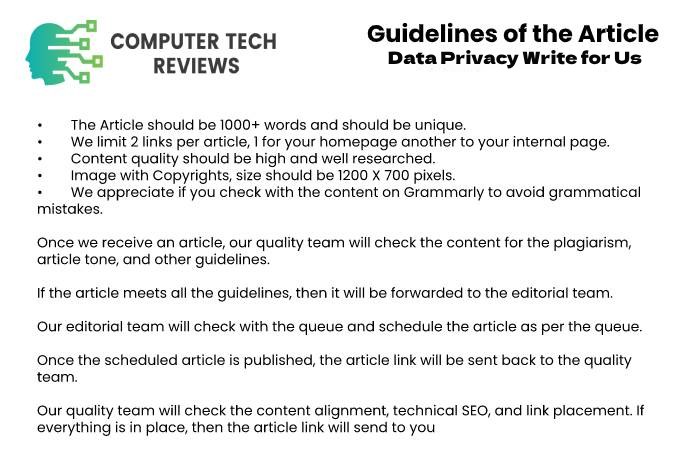
Guidelines of the Article – Data Privacy Write for Us
You can send your article to contact@computertechreviews.com
Related Pages:
Big Data Write for Us
Software Write For Us
Cloud Computing Write For Us
Computer Write for Us
VOIP Write for Us
Data Center Write for Us
Web Design Write For Us
CCleaner Write For Us
SSD write for us
Electronics write for us
iPad write for us
operating system write for us
accounting write for us
wireless write for us
virtual write for us
USB write for us
microphone write for us
Streaming write for us
video promotion write for us
SQL write for us
Recent Posts
The Best Strategies for Chicken Road Players
Welcome to Chicken Road—a fast-paced crash-style casino game built around one core decision: how many steps you’re willing to take…
What is Accessibility? – Definition, Uses, Features and More
Accessibility Definition Accessibility is the quality of what is accessible. The adjective accessible, meanwhile, refers to what is simple understanding…


