Kamran Sharief
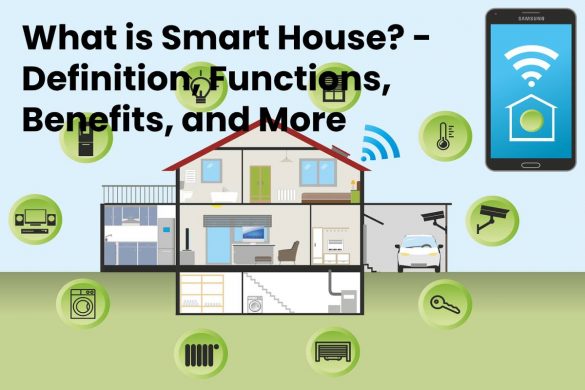
What is Smart House? – Definition, Functions, and More (2025)
Definition Smart House A house with Home automation or domotics is called a [smart house]. A home automation system controls climate, lighting, appliances,…
Versa Networks Multi-Cloud SD-WAN Webinar [2025]
Easy, Safe and Consistent Multi-Cloud SD-WAN Date: Thursday, September 26, 2019 Time: 1:00 pm ET / 10:00 am PT Sponsored…
What is User Experience? – Definition, Usability, And More (2025)
Definition User Experience User experience is a person’s attitudes and emotions about using a particular service, product, or system. It…
What is AJAX? – Definition, Functions, Examples, And More (2025)
Definition AJAX AJAX means asynchronous JavaScript and XML is a set of web development techniques that allow web applications to…
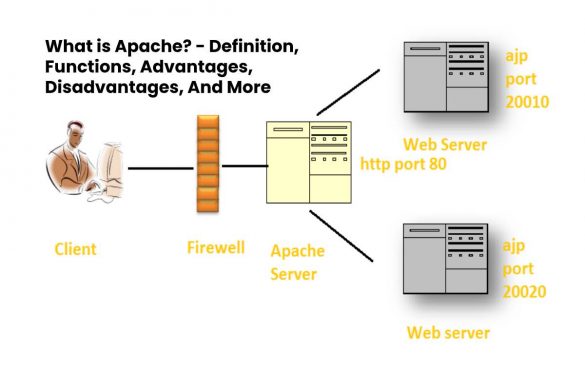
What is Apache? – Definition, Functions, And More (2025)
Definition Apache Apache HTTP is a free Server, open-source web server software for Unix platforms with which 46% of websites…
What is HTTP 404? – Definition, Negatives, And More (2025)
Definition HTTP 404 The 404, HTTP 404, 404 Not Found, Page Not Found, or Server Not Found error message is…
What is Adware? – Definition, Types, Features, And More (2025)
Definition Adware Adware, also known as advertising-supported software, is software that produces income by automatically generating online advertisements in the…
What is Active Server Pages? – Definition, Uses, And More (2025)
Definition Active Server Pages (ASP) Active Server Pages is the first server-side script engine by Microsoft; it dynamically generates web…
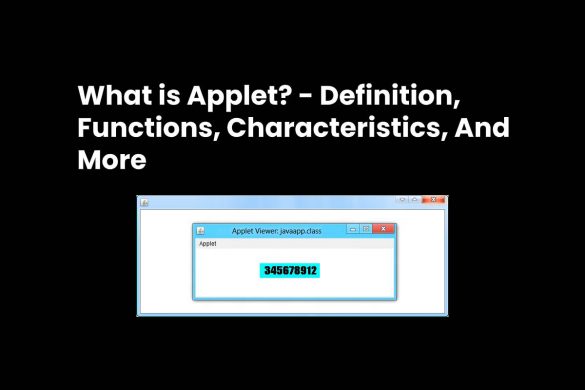
What is Applet? – Definition, Functions, And More (2025)
Definition Applet An applet is a component of an application running in the context of another program, for example, a…
Microsoft Project xCloud: A 360-Degree Overview of the Service [2025]
The internet is a blessing, not a curse as some deem it to be. If it were not for the…
6 Best uTorrent Alternatives for Windows PC – April [2025]
uTorrent Alternatives: Millions of people use uTorrent, yet not of them are happy with this program due to the annoying…
Cut The Cord With The Best Cable TV Alternatives [Top Options for 2025]
Cable TV Alternatives Cable TV has had a monopoly on consumer entertainment for a long time. Millions of Americans tune…