The word polymorphism is used in different settings and portrays circumstances in which something happens in a few unique structures. In software engineering, it depicts the idea that various kinds can be gotten through a similar interface. Each type can give its own, free usage of this interface. It is one of the critical ideas of the article arranged programming (oop).
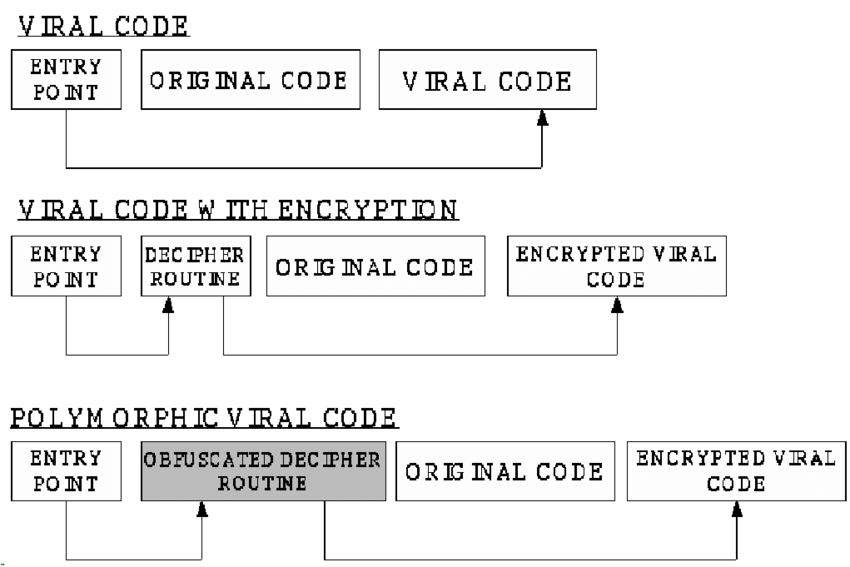
Table of Contents
Various Kinds of Polymorphism
Java supports two sorts of polymorphism:
- static or assemble time
- dynamic
Polymorphic malware
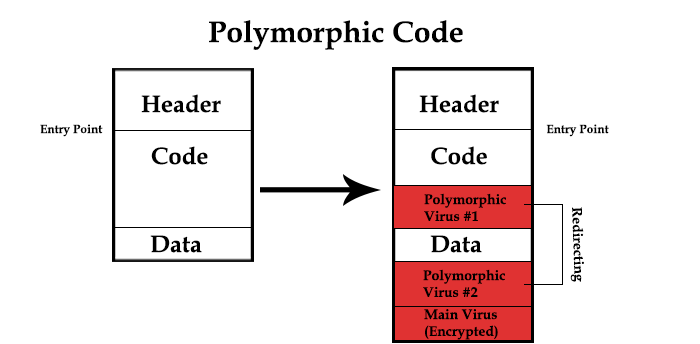
Polymorphic malware is a kind of malware that continually changes its recognizable highlights to dodge identification. Many standard types of malware can be polymorphic, including infections, worms, bots, trojans, or keyloggers. Polymorphic procedures include changing recognizable attributes like record names and types of encryption keys to make the malware unrecognizable to numerous discovery strategies.
Polymorphism is used to sidestep design coordinating discovery depended on by security arrangements like antivirus programming. While specific attributes of polymorphic malware change, its practical reason continues as before. For instance, a polymorphic code will spread and contaminate gadgets regardless of whether its unmistakable changes evade identification. By changing qualities to create another mark, signature-based recognition arrangements won’t perceive the document as vindictive. Regardless of whether the new signature is recognized and added to antivirus arrangements’ unique information base, polymorphic malware can keep changing marks and do assaults without being identified.
Instances of Polymorphic Malware
Webroot specialists have discovered that 97% of malware contaminations utilize polymorphic procedures. While many of these strategies have been around since the 1990s, another influx of destructive polymorphic malware has developed over the previous decade. Some prominent instances of polymorphic malware include:
- storm worm email: the scandalous spam email sent in 2007 with the subject “230 dead as tempest hitters europe” was, at a certain point, liable for as much as 8% of all worldwide malware contaminations. When the message’s connection is opened, the malware introduces wincom32 administration and a trojan onto the beneficiary’s pc, changing it into a bot. One reason the tempest worm was so difficult to recognize with regular antivirus programming was the malignant code used transformed like clockwork or something like that.
- crypto wall ransomware: the crypto wall is a polymorphic ransomware strain that scrambles documents on the casualty’s pc and requests a payoff installment for their decoding. The polymorphic developer used in a crypto will is used to create another variation for each expected casualty.
Static Polymorphism
Similarly, as other articles situated programming dialects, Java permits you to execute various strategies inside a similar class that similar utilization name yet an alternate arrangement of boundaries. That is called strategy over-burdening and speaks to a static type of polymorphism.
The boundary sets need to vary in any event one of the accompanying three rules:
- , they need to have an alternate number of boundaries; for example, one strategy acknowledges two and another three boundaries.
- the sorts of the boundaries should be extraordinary; for example, one technique acknowledges a string and another along.
- they need to anticipate the boundaries in an alternate request; for example, one technique acknowledges a string and a long, and another acknowledges a long and a string. This sort of over-burdening isn’t suggested because it makes the API hard to comprehend.
Much of the time, every one of these over-burden strategies gives an alternate, however fundamentally the same as usefulness.
Because of the various arrangements of boundaries, every technique has an alternate mark. That permits the compiler to recognize which technique must be called and tie it to the strategy call. This methodology is called static official or static polymorphism.
Dynamic Polymorphism
This type of polymorphism doesn’t permit the compiler to decide the executed technique. The job needs to do that at runtime.
Inside a legacy progression, a subclass can abrogate a technique for its superclass. That empowers the engineer of the subclass to redo or supplant the conduct of that strategy.
It additionally makes a type of polymorphism. The two strategies, actualized by the super-and subclass, share similar names and boundaries yet give diverse usefulness.
Conclusion
Polymorphism is one of the central ideas in oop dialects. It portrays the idea that various classes can be used with a similar interface. Every one of these classes can give its execution of the interface.
Java upholds two sorts of polymorphism. You can over-burden a strategy with various arrangements of boundaries. It is called static polymorphism because the compiler statically ties the strategy call to a particular technique.
Inside a legacy chain of command, a subclass can abrogate a strategy for its superclass. On the off chance that you launch the subclass, the JVM will consistently call the superseded technique, regardless of whether you cast the subclass to its superclass. That is called dynamic polymorphism.