Table of Contents
What is XSS?
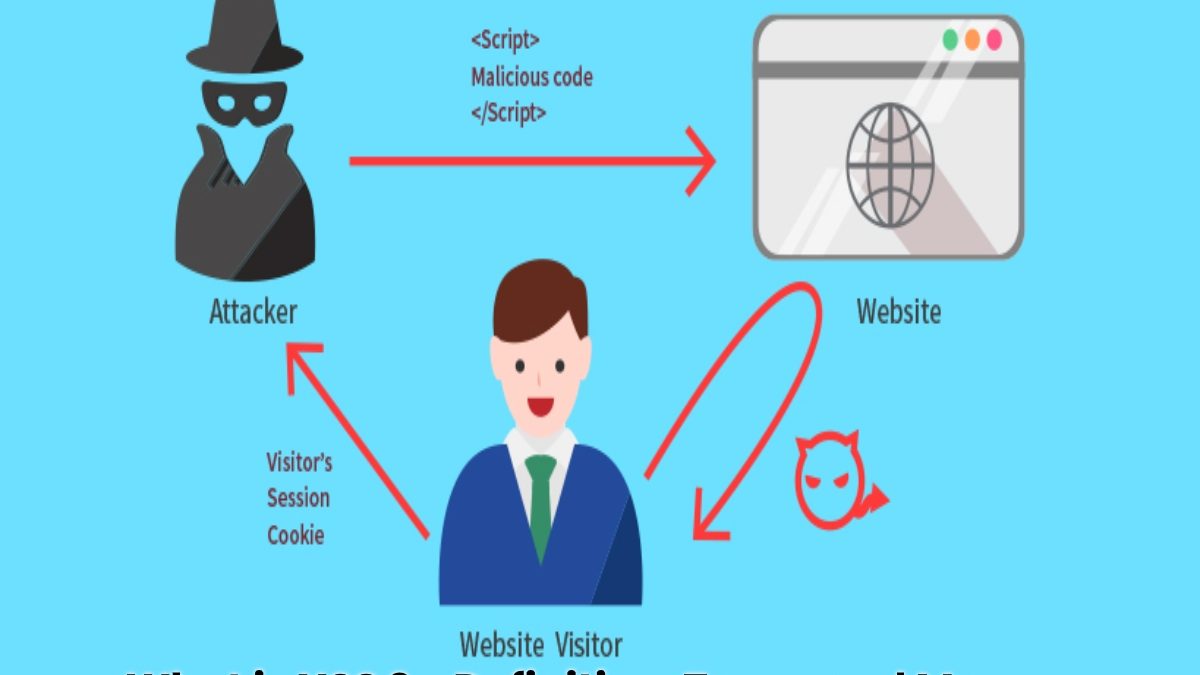
XSS (Cross-site Scripting) is a code injection attack that allows an attacker to execute a malicious script in a dynamic web application.
It attacks aim at the code (also called a script) of a web page that runs in the user’s browser, not on the website’s server. When there is an attack on the users, it introduces malicious scripts into your browser that will attempt to damage your computer.
The variety of XSS attacks is virtually unlimited, but the most common is usually the collection of personal data, the redirection of victims to sites controlled by hackers, or the control of the equipment by them.
How do Cross-site Scripting attacks occur?
- Websites save data and send information to your browser continuously. XSS attacks occur when untrusted sources send malicious content to users’ browsers through website vulnerabilities.
- This malicious content can then steal data from your computer or damage your system. For example: when a user searches something online, the website sends information to the browser in the form of search results.
- In an XSS attack, the information received may contain malware that could steal your data. Since virtually all websites need to save and send data to browsers, XSS is the most common security breach in software today.
How to prevent XSS?
Since XSS attacks occur due to code injections, it is necessary to handle the information entries that the application will use correctly.
All input parameters must validate correctly and filtered according to different criteria. The treatment of this data can be:
- Filter: Based on regular patterns or expressions, determine what type of data the system accepts and which does not.
- Escape: Accept all types of data, but escaping them correctly.
- Clean up: Accept all types of data, but remove inappropriate content.
- Transform: Accept all types of data, but transform them into an accepted type of data.
We must understand the difference between these different methods since it must adapt to the operation of the application.
For example, if we have a rich text editor, through which the user is allowed to manipulate HTML code. In this case, we should not opt for the option to escape the characters since at the time of displaying the information the browser will not interpret it and It will show it as text.
Types
There are mainly three types of XSS, and they are cataloged according to the way they operate:
- XSS reflected: an attacker sends a link that redirects to the site affected by the vulnerability. This link contains the embedded code that will be executed when the victim opens the link.
- Persistent XSS: An attacker inserts a script that remains on the website and every time a user visits the site. He will execute the code in his browser.
- XSS on DOM objects: This attack does not require HTTP requests. The embedded script is the result of modifying the DOM of the Web site. And executes it in the victim’s browser.